Suspected North Korean Hackers Infiltrate Google Play With ‘KoSpy’ Spyware
A newly uncovered spyware campaign, believed to be linked to North Korean cyber attackers, has been discovered on the Google Play Store. This malware, named “KoSpy,” was disguised as innocent utility applications but secretly gathered extensive personal information from infected Android devices, including text messages and screenshots, according to cybersecurity firm Lookout Mobile Security.
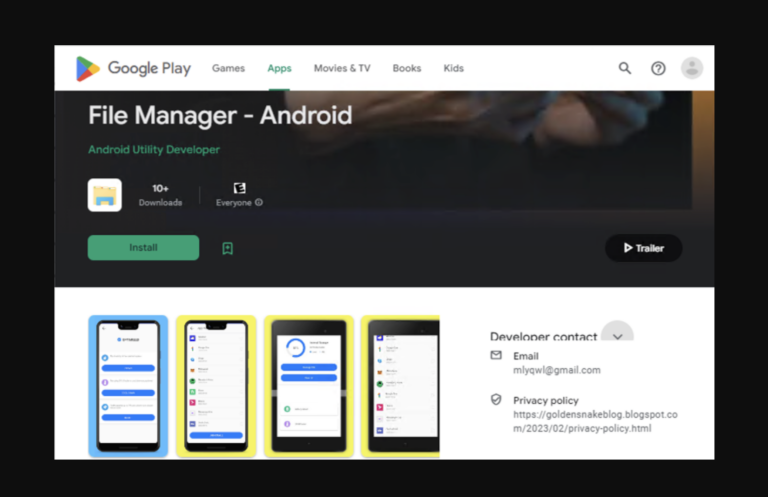
Lookout has expressed moderate confidence that KoSpy is connected to North Korean hacker groups such as APT37 (also known as ScarCruft), which is notorious for cyber espionage operations. The spyware targeted apps available in both Korean and English and appeared on Google Play under the guise of an app called “File Manager – Android.” Google has since removed this app, which reportedly had fewer than 10 downloads.
A Google spokesperson explained that the presence of regional language in the apps suggested a targeted attack. They confirmed that the malware sample, which surfaced in March 2024, was promptly taken down before any user installations occurred. Google Play Protect continues to safeguard Android users by blocking known versions of this malware, even when apps are installed from outside sources.
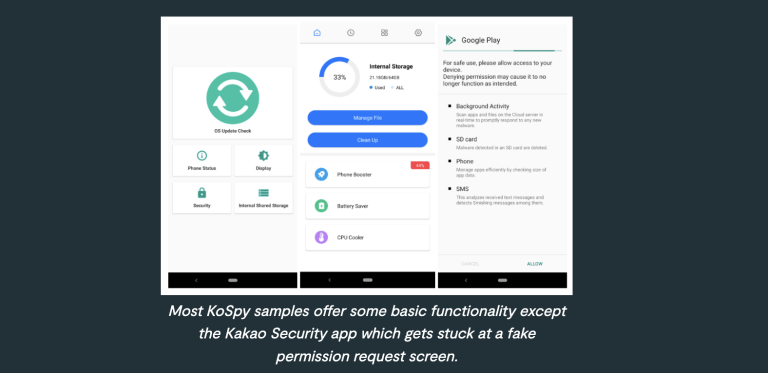
Lookout identified KoSpy operating under five different names: 휴대폰 관리자 (Phone Manager), File Manager, 스마트 관리자 (Smart Manager), 카카오 보안 (Kakao Security), and Software Update Utility. These fake apps usually presented simple interfaces that allowed access to the device’s internal settings, while others displayed basic system windows requesting device permissions as a ruse.
Once installed, the spyware covertly connects to hacker-controlled servers and downloads additional malicious plugins aimed at spying on the device and extracting sensitive data. KoSpy could also tailor its messages to the user in either Korean or English, depending on the target.
Although samples of KoSpy date back to at least March 2022, the most recent specimen was obtained in March 2024. The command and control servers associated with the spyware are currently inactive, suggesting KoSpy may no longer be operational. Lookout noted that some versions of KoSpy were also found on third-party app stores like Apkpure, but none remain available on the official Google Play Store.
Google confirmed that all identified malicious apps were removed from its platform, and their related Firebase projects were shut down. Lookout further linked KoSpy to APT37 because one of the domains contacted by the spyware resolves to an IP address in South Korea previously tied to APT37 and another North Korean hacking group, APT43.
Lookout highlighted the challenges in definitively attributing such attacks, stating that North Korean threat actors often share infrastructure, targeting strategies, and operational methods, which makes pinpointing a specific group difficult.